BeyondTO GameGuard: A Modern Watchdog for Talisman Online Security
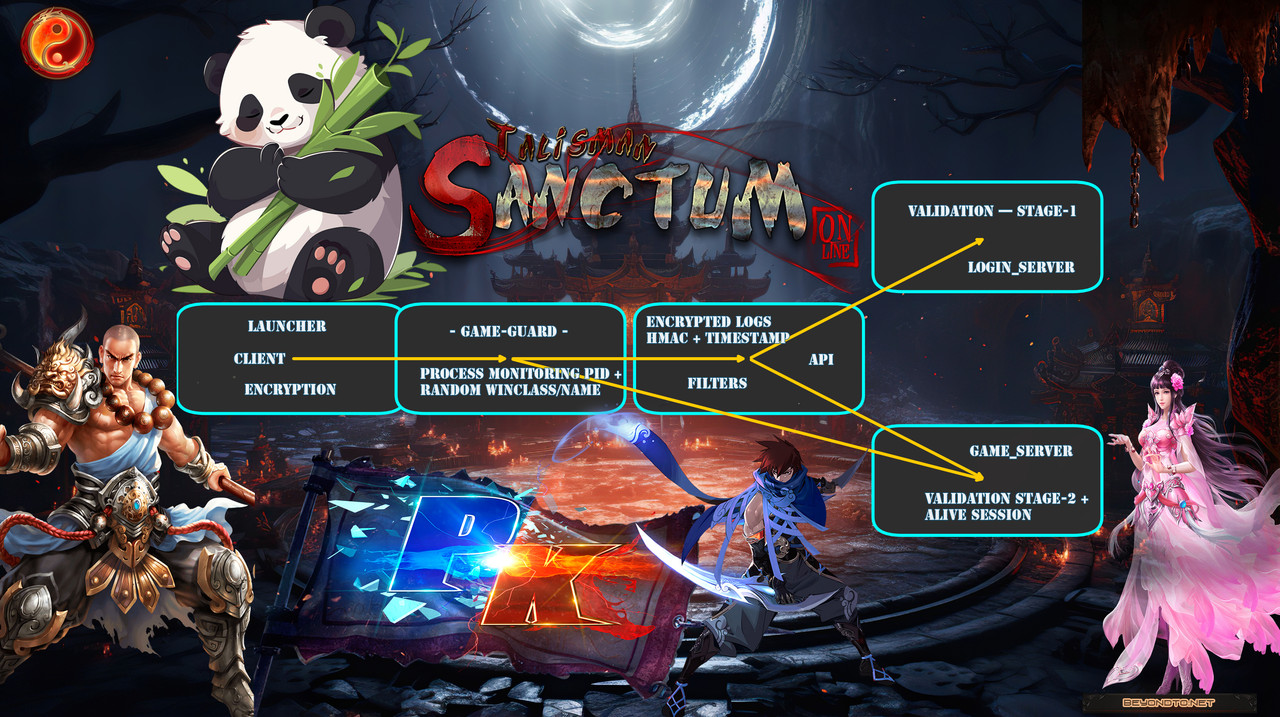
GameGuard is not a standalone tool—it’s tightly woven into the same communication channels and encryption layers that the game itself uses. This ensures that client–server communication remains seamless and secure. (Non-native function of the game)
Login Server: Validates the session before allowing entry.
Game Server: Maintains continuous verification throughout gameplay.
API Layer: Acts as the bridge for logging, validation, and real-time checks.
All of this runs through the exact same secure pipelines the game already trusts, avoiding weak “side channels” that cheaters often exploit.
🛠 Hard Unpacking & Environment Control
To even reach this stage, the client undergoes hard unpacking and import rebuilding, ensuring that traditional reverse-engineering tools hit a brick wall.
Fully unpacked + rebuilt a lot of sections to make this happen (both sides bypassed — Client / Server).
Removed Anti-Robot sections (from the past original Themida build).
UI & Engine Console Disabled: No debug text, no hidden menus—attackers can’t use built-in consoles or logs against you.
Clean Surface: By stripping these outputs, the attack surface shrinks drastically.
Human verification is enforced at the UI level itself. C++ / Lua 5.0 / proper .XML injections + XOR encryption.
Captcha windows are called through EvUI dispatcher events.
This makes it part of the native flow of the game engine, not an external overlay—ensuring authenticity and preventing bypass.
At the heart of the guard lies the Watch Dog driver, constantly monitoring the health of the game client:
PID Tracking: Ensures the protected process remains alive.
Randomized Window Name & Class: Since Themida repacks client.exe with randomized identifiers every launch, GameGuard dynamically detects them and tracks the process reliably.
Client 1553 build has a fixed class name.
Client 1635 build (with two releases, 2009 and 2010) gets randomized at runtime—the watchdog executable grabs it dynamically.
Client 1652 build works with both 1635 executables.
TCP Alive Session: Guard and server maintain a live session. If GameGuard halts, freezes, or is killed, the game connection is dropped.
Cheaters often poke memory to inject hacks—but GameGuard has teeth:
Monitors protected address regions.
If a debugger or unauthorized tool touches them → the guard instantly terminates the game (and all logs are uploaded to the API).
This protects both gameplay logic and sensitive runtime data.
Security is not just client-based—it’s mirrored server-side:
Complete Logging: Every event is logged. (On a suspicious attempt to log in from an unauthentic client—tampered or running outside the guard—we do not kill the session; we keep it alive for a while… that’s where the magic happens).
Fail2Ban Compatibility: Logs integrate with standard Linux tools for automated banning.
Extended Reports: GameGuard sends HMAC-signed logs with timestamps, IP address, hardware IDs, and more.
Hardware Ban: Persistent offenders can be locked out at the hardware level.
Traditionally, admins only had server-side GDB traces to analyze crashes or attacks.
Now, GameGuard also reports from the client side:
Pinpoints which memory addresses were affected.
Provides real-time feedback about what triggered the guard.
Result: Developers get two perspectives at once (server + client), making hotfixes dramatically faster and more precise.
✔ Encrypted API, Login & Game Server integration
✔ Hardened unpacking with imports rebuilt
✔ Console & UI debug output fully disabled
✔ Captcha integrated via native EvUI + Lua 5.0 dispatcher calls
✔ Watch Dog driver tracking PID + randomized window class/name
✔ TCP alive sessions—disconnects if guard is halted
✔ Virtual memory address protection (instant kill on tamper)
✔ Fail2Ban-ready server logs
✔ Client log uploads (HMAC, timestamp, hardware info)
✔ Hardware ban system
✔ Dual-sided error reporting for faster hotfixes
✔ All Guard System Integrated (Teleport / Game Mall)
---
### On-Going Work
- GameGuard Watch has high RAM usage on older Windows 10 builds and Windows 7 (XP and Windows 8 are fixed; Windows 11 not tested).
- Removing the encryption method due to problems with Microsoft SystemCertificates (it will now be delivered from a remote session instead of using WinCrypt).
- Updating issues related to db_server duplications globally. Instead of Lua or workaround fixes, a global fix via binary patch will be applied.
- Removing a lot of junk packets from 1652 client files to reduce EvNet errors on the login terminal.
- Replacing packing VM RedTiger with a lighter VM (to decrease false-positive detections).
- Several in-game tests required due to major client–server packet changes.
---

